Is a VPN The Answer?

With COVID-19 keeping everyone inside for the last few weeks, I’ve been getting a lot of questions from friends about VPNs from and if they are worth the investment. My answer has always been the same, “Oh shit, well, umm I will try and write a blog about it.”
Because it’s never that simple, it’s never a yes or no scenario. Everything comes down to the nuances of your specific use case and threat model. What are you doing, what are the risks, and what are you trying to prevent?
I was having a conversation with a friend a few days ago about his home network and he mentioned he was in the middle of buying a router and then flashing the operating system to install DD-WRT, and then he was going to route his entire network through a VPN in another country and then also bring Tor into the mix while at the same time, he was a self confessed novice at networking, This was a “solution” recommended by a security friend.
“What are you trying to do?”, I asked.
“Oh just trying to protect my data, from my ISP selling it, privacy and all you know?”
My reaction would have been the same if my 63 year old mother called me to tell me she’s rebuilding a transmission of her car. I get it, but given her situation and knowledge of the subject matter, it might be better to just look into another solution if she’s just looking to drive.
It’s very common for security marks to recommend moonshot security solutions for people not too tech savvy. Part of it is just a little disconnection from regular people’s use case, part of it is gate keeping bullshit which is another blog post for another time, but when someone lacks an understanding of the back end functionality of the technology and various externalizes, they could find themselves implementing a solution that actually could make them more exposed.
So, if the use case is ensuring your privacy and preventing your web browsing from being “sold off”, do VPNs like NordVPN, PrivateInternetAccess or ExpressVPN do it?
To answer that we have to go over just how internet connections are made.
On a default setup, if I were to type pornhub into my address bar, my computer would query my ISP’s DNS (Domain Name System) server for the IP address. My ISP would then respond back with the IP address it either had in its cache or it would query another server downstream to get the address. Upon receiving the IP address (66.254.114.41) from the DNS server, my computer that would then initiate a connection to it. This whole back and forth happens totally unencrypted with your ISP. Every single .com, .org, or any other website name address that your computer queries, whether by you manually entering it in the url, or queried by ads, or any other application on your computer is done via plain text and is viewable by your ISP, like below
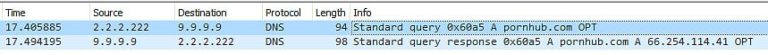
Utilizing a VPN, my ISP would only see an encrypted connection to the VPN’s server, but the VPN would still be able to see everything my ISP used to see which means that at its core, utilizing a VPN for privacy is just a shift in trust. Now, for many, that shift in trust is a quick simple assessment but the bigger, more centralized problem with VPNs is that they’re being oversold as silver bullet solutions for many unsuspecting consumers and constantly parade around incredible claims. Now, if a VPN has no problem being deceptive with how a VPN operates and their effectiveness to me, why on earth would I believe their claim that they take my privacy seriously when they don’t even take me seriously?
Snake oil and homeotherapy may be too strong of analogies, because VPNs do actually have a legitimate use in some circumstances way they are pushed in online marketing, VPN ads are beginning to rival end time evangelical preachers in terms of their far fetched claims and fear mongering. Go to any VPN site, they probably will say something on that webpage like, “YOU ARE NOT PROTECTED” on their page because your IP isn’t using their service. That’s all those web pages check for. There’s no other magic happening where your computer is scanned and has a hole. It just means, you’re not a customer.
If you recently ponied up a bunch of money for a VPN, you will probably claim that your VPN doesn’t log and I would say your VPN probably has a nice website that says that it doesn’t log, but because neither you or I are able to see firsthand the infrastructure and validate it’s practically meaningless. Many VPNs have to rely on a basic set of logging to enforce device limits and other controls. Even if they do have audits and fancy badges on their site to prove they don’t log, that doesn’t mean that someone else isn’t monitoring the infrastructure those VPNs are on. And before you ask, yes, there have been VPNs like H.M.A that have given up their users before, so why would any others stand up for 1 user in the face of a subpoena?
If you’re not too tech savvy, the reason you’re probably thinking of a VPN is because you saw an advertisement or a promotion that really seemed enticing, or some youtuber or blog included in in a post. If you google ‘VPNs’, half of the results are entire websites dedicated to top 10 reviews of VPNs, that’s literally just an interactive ad. Be aware, despite flashing an impressive perception that a VPN gives off due to marketing or reviews, some companies are involved in shadier practices behind the scenes. While others have been involved with producing malware. So don’t automatically assume a VPN has your best interests at heart just because they come off very honest. Some VPNs were found to deceive and inform the users that they were routing their data through one IP address when actually on the back-end they were being actually being routed through another. Suddenly that initially quick and simple shift in trust isn’t looking so simple.
VPNs can not be assumed to be a fully effective way of hiding your identity either. If you login to the same services while logged into the VPN. Using aggregation from a number of other data points can be used to identify you, I offer up this 2016 criminal complaint in the US District Court for cyberstalking. The defendant had a computer science degree and was well aware of how VPNs operated and he was still able to be identified.

Imagine that, a pitch to be this super private, anonymous service that is the perfect honeypot for those with more “interesting” traffic only to track it all anyway. I’m not a tinfoil hat conspiracy theorist, but the the assertion that many VPNs could be honeypots is a reasonable one. The amount of money spent within the technology media spheres advertising and seeking out those looking for people looking to hide should cause one to at least reflect on the possibility of it.
If hiding from the government is more your thing, if the VPN is headquartered in the Five Eyes or the Fourteen Eyes countries, it’s subject to data retention laws. That is why the U.S. and U.K.-based VPNs are generally not recommended by privacy-protection organizations and security experts.
You could probably find one ran out of a shack in Iceland that really protects your privacy, but then come the questions about reliability, network speed, etc. “I’m so glad I have this gigabit internet connection routed through a 50Mbps VPN in Iceland.“
Creating a VPN isn’t hard. I mean it is for a non technical person, but it’s not as hard as an entire company being dedicated to it would make one believe. If someone had internet access to their meth lab in Barstow, they could technically run a VPN server and sell access from a fancy looking website pumped up by Reddit reviews and we might not even know the difference. Hell, the VPN could be a front run by an adversarial state and we wouldn’t know the difference.
I’m not saying VPNs don’t ever serve a purpose, there are plenty of proper reasons to utilize a VPN and in fact, I’ve previously written about using some of them. My main use of VPNs are to tunnel between devices so I can stream with more stability. My work has a VPN so I can access that network over an encrypted connection. Other legitimate uses are for tunneling through untrusted public networks like starbucks or an airport, or even bypassing government blocks or geolocked content.
I’m also not saying that all VPNs are bad either. There may be some that legitimately don’t log your activity, who’s client isn’t malware, or have security issues, or who’s network isn’t externally monitored themselves, or who’s client doesn’t leak your DNS requests back to your ISP, or who’s infrastructure doesn’t slow down your speed, but it will take a lot of time researching and finding it. Thatoneprivacysite.net probably has the most definitive listing and ranking of them. I know a couple people who opt in spinning up their own on the own server they know doesn’t log, but what about the network those servers sit in? I don’t know if you can find that unicorn solution that hits 100% of those checkboxes and ensure total 100% privacy, because at at the end of the day, its still just a shift in trust. For some, that shift brings with it more cans of worms than not.
Everyone has their level of risk tolerance, or the amount of risk they’re willing to be exposed to (or own) before they take an action to remediate it if at all. Some aren’t comfortable with their ISP and to them and their situation, it makes sense. Others, might not.
Now, I write from the United States and the reputation of ISPs here is far worse than other places. Many of the things ISPs do here with customer data is considered illegal in other countries. However, at the same time, the amount of censorship that’s other countries experience which warrants a VPN is far worse. I would say that US ISPs still have more to lose than a random VPN that could be run by some college kids in Serbia with a nicely designed logo. If you’re worried about ISP specific DNS Blocks you can update those to alternative ones, but remember, that’s sharing those unencrypted DNS requests with those new DNS revolvers now.
I know what you’re probably asking in your head, isn’t there something I can do that’s more impactful than simply changing my IP via a VPN that would help protect my data?
Sure, but unfortunately it’s not as fun and exciting installing an application with a big fancy padlock that says ON when you start it. It’s actually a little time intensive, but if you live in California like I do, you can legally request ISPs and other companies not to sell your data to marketers and you should track down every single CCPA portal for every company you know that has a data profile on you and you should opt out.
I know these are mostly effective because the amount resources the previous companies I’ve been employed at spent to comply with this and GDPR were extensive because the penalties for not complying are real.
For example, here’s Spectrum’s opt out website for CA residents.
Here’s Frontier’s, which is a little more of a hoop to jump through.
T-Mobile’s here, you should google the company name and “opt out ccpa” to try and find any company you know that might have a data profile on you.
What if I’m outside of California? Check with the laws in your local jurisdiction for the privacy implications and data collection laws. Definitely look into at least encrypting your DNS requests with DNS over HTTPS or DNS over TLS. Install uBlock on your browser or look into setting up a Pi-Hole which either would actually be more impactful by killing tracker requests than a VPN which would just route those same requests from another IP.
Furthermore, many who ask the VPN question do so before taking more meaningful steps to protecting their privacy and securing their data such as assessing their data footprint or account vulnerabilities with a password manager. Or going down and turning on 2FA on all the applicable accounts, or ensure all your programs and browsers are patched and updated.
At the end of the day, is a VPN the answer? Well, it still depends, I mean if the question is a tunneling one, then probably. If the question is looking for a simple privacy solution or to be a silver bullet for your entire risk portfolio that many VPNs are guilty of masquerading as then you are going to be disappointed.
— Further Reading:
https://www.reddit.com/r/VPN/wiki/beware_of_false_reviews
https://krebsonsecurity.com/2017/03/post-fcc-privacy-rules-should-you-vpn/
https://gist.github.com/joepie91/5a9909939e6ce7d09e29
https://www.engadget.com/2017-04-07-good-luck-finding-a-safe-vpn.html
https://drewdevault.com/2019/04/19/Your-VPN-is-a-serious-choice.html
https://www.natlawreview.com/article/ccpa-qotd-what-are-penalties-non-compliance-ccpa
https://www.makeuseof.com/tag/avoid-bad-vpns/
https://schub.wtf/blog/2019/04/08/very-precarious-narrative.html